
Wireless is Not Mission Critical
On this episode, Tom Hollingsworth and the panel discuss how the world is more wireless that ever and if it’s reliable enough in critical situations.

On this episode, Tom Hollingsworth and the panel discuss how the world is more wireless that ever and if it’s reliable enough in critical situations.

Attackers are starting to target the critical infrastructure that runs industrial and manufacturing facilities. That may not sound like a new thing but the speed and sophistication with which they’re increasing their attacks is. Security firm Dragos hast noted in a recent post that there has been a significant increase in the number of people using password cracking tools on industrial equipment such as programmable logic controllers (PLCs). Where the real devilish genius comes into play is not tha these attackers are trying to corrupt them. Instead, they’re converting these machines into nodes in large botnets to amplify attacks. And if you think it’s hard to clean a malware infection from a PC try doing it on a PLC that can’t be shut down. Dragos noted that while they only tested one particular kind of PLC many other samples had traces of malware infections. Stephen, is this going to cause issues for our already strained supply chain?

Apple has quietly added a new “Lockdown Mode” to iOS 16, iPadOS16, and macOS Ventura that allows users to restrict the channels often used by the most intrusive exploits and hacks. It’s designed to protect journalists, dissidents, and others at risk of state-sponsored snooping. This and more on this week’s Rundown. Head to GestaltIT.com for shownotes.

In this episode, our group of wireless experts discuss the premise and whatever or not we are Using the Words Site Survey Wrong.

We’re back with more mobility and wireless content at Mobility Field Day 7!

NIST has announced their selections for quantum-safe encryption algorithms. The competition has been running since 2016 when the standards body realized that quantum computing could potentially impact RSA-based public key encryption. The new encryption method, CRYSTALS-Kyber, as well as digital signature methods named CRYSTALS-Dilithium, FALCON, and SPHINCS+, are designed to be implemented in the coming years for highly senstive data that could come under attack from advanced threats as well as the inevitable future of a powerful factoring system like a quantum computer. Are we all going to have to get new key tokens now?

The artificial intelligence community is buzzing about the just-released ML Commons MLPerf Training v2.0 results, which were announced today. NVIDIA, Intel Habana, Google, and Graphcore all submitted at least partial results, and everyone is crowing about their performance. NVIDIA is the only one to cover the field, and has a strong showing despite still relying on their A100 GPUs. Intel’s Habana Gaudi 2 also shows great performance per watt in the tests they submitted, with the Graphcore Bow IPU and Google TPUv4 trailing somewhat. How do we make sense of all this ML training hardware? Head to GestaltIT.com for shownotes.

In this episode, sponsored by Fortinet, Tom and his panel discuss why Consistent Security is Hard.
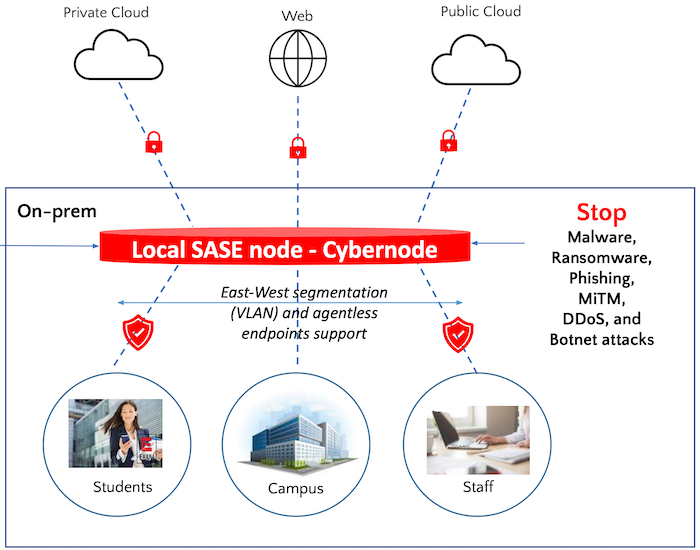
Can you deploy XDR in the mid-market? Is there a budget for doing advanced security in an SME? Tom Hollingsworth looks at the latest offering from Exium that is aimed at bringing advanced security where it’s needed most.

Is hybrid cloud still a popular choice for users? Are there good reasons to keep data local as opposed to moving it somewhere else? And does multi cloud play a role at all? Find out what I think about it in this episode of Tomversations.