Cisco Integrates Accedian into Crosswork to Deliver Uninterrupted Service Assurance
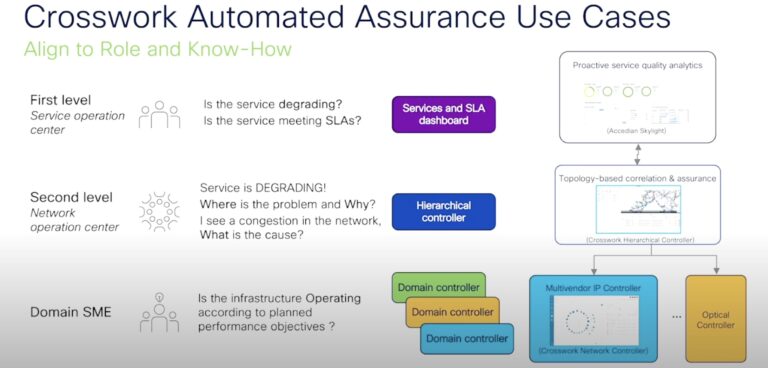
At the Tech Field Day Extra at Cisco Live EMEA 2024, Cisco demoed a solution that helps operators overcome these challenges consistently, and deliver flawless quality of service (QoS) to the users. Cisco taps into the capabilities of Crosswork and Accedian to provide teams managing massive-scale multivendor, multi-domain networks a freeway to automated network assurance. Sulagna Saha discusses in this article on Gestalt IT.